AI-assisted interviews are transforming hiring—but they also raise new security risks. Learn how AI impacts data safety, fraud detection, bias, and interview integrity.

Abhishek Kaushik
Nov 27, 2025
As candidates increasingly use AI tools to assist during interviews, the attack surface of hiring has shifted. What used to be a people-and-process challenge is now a software-driven identity and authorship challenge, where fraudulent skill presentation can occur without visible behavioral cues.
Remote interviewing environments make it easier for candidates to outsource reasoning, rely on AI-generated answers, or even let a proxy represent them.
Security teams now recognize hiring as a data integrity system. The interview is not simply a conversation.
It is the primary input into performance predictions, workforce reliability, and operational stability. If this input is compromised, the organization risks downstream productivity loss, regulatory exposure, and undetected insider risk.
Several global enterprises reported material mis-hire losses from candidates who passed interviews using AI scaffolding but failed within the first 60 to 180 days. Failure costs included attrition replacement, team slowdown, and security clearance delays.

Threat Model for AI-Assisted Interview Environments
Threat Category 1: Identity Substitution (Proxy Interviews)
A more skilled person takes the interview for the candidate.
Impact: Role performance does not match demonstrated interview performance.
Threat Category 2: Real Candidate, Borrowed Reasoning
The candidate uses AI tools to answer real-time questions.
Impact: Evaluation measures verbal fluency, not underlying ability.
Threat Category 3: AI Whisper Coaching
Candidate receives real-time answer scaffolding via earbuds or hidden chat overlay.
Impact: Interviewer observes correct statements but no demonstrated thinking.
Threat Category 4: Voice and Persona Deepfakes
Candidate uses synthetic voice or filtered video identity.
Impact: Weakens identity trust and onboarding security baselines.
Threat Category 5: Reference, Code, or Work Sample Plagiarism
Candidate presents past work or repos they did not contribute to.
Impact: Misrepresentation leads to long-term productivity risk and knowledge gaps.
Security Impact Areas
Impact Area | Description |
|---|---|
Productivity Loss | Teams unable to rely on demonstrated skills experience delivery bottlenecks |
Compliance & Fairness Risk | Interview outcomes become legally indefensible if evaluation is distorted |
Insider Access Risk | Hiring into privileged environments without verifying authenticity increases exposure |
Onboarding Failure Costs | Replacement, retraining, and morale loss drive real financial consequences |
AI assistance does not always mean fraud. The risk comes when authorship and reasoning are obscured.
Required Control Shift
Traditional controls focused on watching candidates. Modern controls must focus on verifying authorship of reasoning.
This requires thinking verification, not behavioral monitoring.
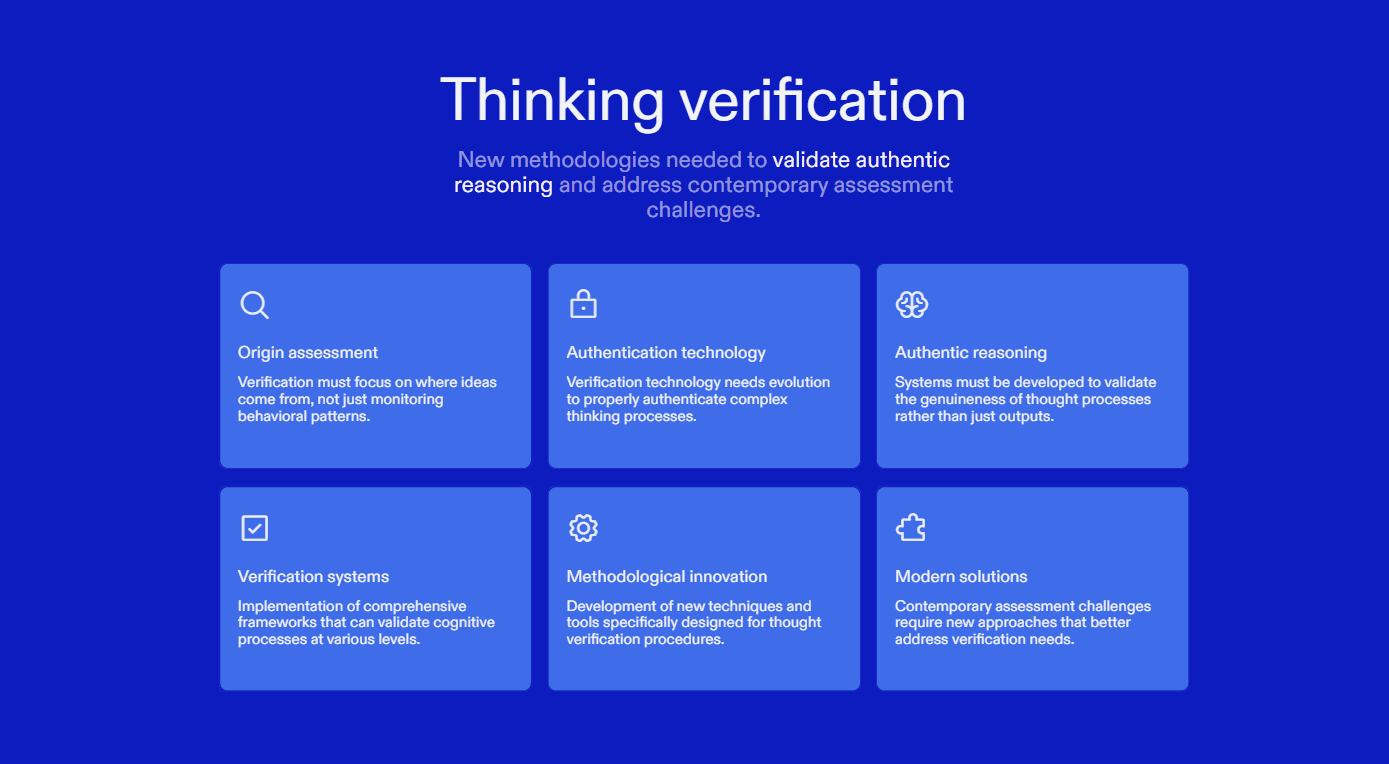
Control Categories and Recommended Implementations
1. Identity Assurance
SSO enforced interview join and unique link access
Passive behavioral identity continuity across rounds
No reliance on manual visual confirmation alone
2. Reasoning Authorship Verification
Require candidates to re-explain concepts in alternate framing
Evaluate ability to translate knowledge across context, not recall
Use interview platforms that measure reasoning continuity (example: Sherlock AI)
3. Structured Interview Notes and Scorecards
Replace free-form narrative with structured criteria-based evaluation
Log follow-up prompts and reasoning evolution
Produce evidence trails to support defensibility
4. Audit and Access Governance
Every interview access event logged
Export or download events monitored
SCIM provisioning to immediately revoke access when roles change
5. Candidate Transparency
Communicate that interviews measure reasoning, not performance theater
Avoid adversarial monitoring posture
Allow candidates to ask about privacy and processing
Candidate trust improves when transparency increases and surveillance decreases.
Where Sherlock AI Fits in This Threat Model
Sherlock AI does not attempt to detect cheating through webcam scanning or keyboard monitoring. It verifies:
Sherlock AI Capability | Security Value |
|---|---|
Identity and authorship continuity | Stops proxy representation risk |
Reasoning adaptation measurement | Identifies borrowed or AI-generated answers |
Structured notes and scorecards | Ensures auditability and fairness |
Transparent candidate experience | Prevents adversarial or biased interviewing dynamics |
This approach maintains evaluation accuracy, legal defensibility, and candidate fairness simultaneously.
Closing Insight
Hiring is now a security surface. Organizations must shift from:
Monitoring behavior
toVerifying authorship, reasoning, and identity continuity
This is not about catching candidates. It is about ensuring the signals used to make staffing decisions are real, defensible, and predictive.
The future of secure hiring is transparent, structured, and authorship-aware.



