Discover how Interview Integrity compares to Zero Trust in modern hiring. Learn key differences, risks, and why both matter for fraud-free, trustworthy interviews.

Abhishek Kaushik
Nov 27, 2025
Zero Trust frameworks assume that no identity, behavior, or access state should be trusted by default. Every interaction must be verified continuously. The same logic now applies to hiring. With remote interviews, AI-assisted answers, whisper coaching, and proxy participation, hiring teams face the same identity and authorship risks that cybersecurity teams addressed years ago.
Interview Integrity is essentially the Zero Trust model applied to skill verification and candidate identity.
Hiring cannot assume:
The person on camera is the person being hired
The answers reflect the candidate’s own reasoning
The voice or face is unmodified
The explanation reflects reproducible, job-ready ability
The only defensible approach is verify, not assume.
Zero Trust is now the default security stance across federal, defense, and enterprise IT. Hiring workflows are one of the last identity surfaces operating on trust by default.

Zero Trust Pillars and Their Equivalent in Interview Integrity
Zero Trust Pillar | Security Definition | Interview Integrity Equivalent | Example Control |
|---|---|---|---|
Verify Identity | Never trust identities by default | Confirm the candidate is the person presenting the reasoning | Identity continuity and authorship verification (Sherlock AI) |
Verify Context Continuously | Trust must be evaluated in real time | Evaluate reasoning under shifting prompts | Re-explanation tests and adaptability checks |
Least Privilege Access | Only grant necessary access | Interviewers see only relevant data to evaluate fairly | Role-based access controls and limited interviewer views |
Explicit Logging and Telemetry | Everything must be traceable | All interview access, edits, and notes must be auditable | Audit logs for access, scoring, and data export |
Assume Breach | Design controls expecting compromise | Expect candidates to have AI assistance and adjust evaluation accordingly | Reasoning pattern detection rather than cheat detection |
This framework removes the idea of “catching” people and focuses on continuous validation of authenticity.
Read more: What Is Interview Integrity and Why It Matters
Why Traditional Interviewing Violates Zero Trust
Traditional interviewing assumes:
Face presence equals identity
Fluency equals expertise
Confidence equals readiness
One-time answers reflect stable knowledge
These are trust-by-default assumptions. Zero Trust requires evidence-by-default.
In mis-hire audits from large distributed engineering teams in 2024 to 2025, the majority of failures came from overestimating candidate independence based on confident interview performance.
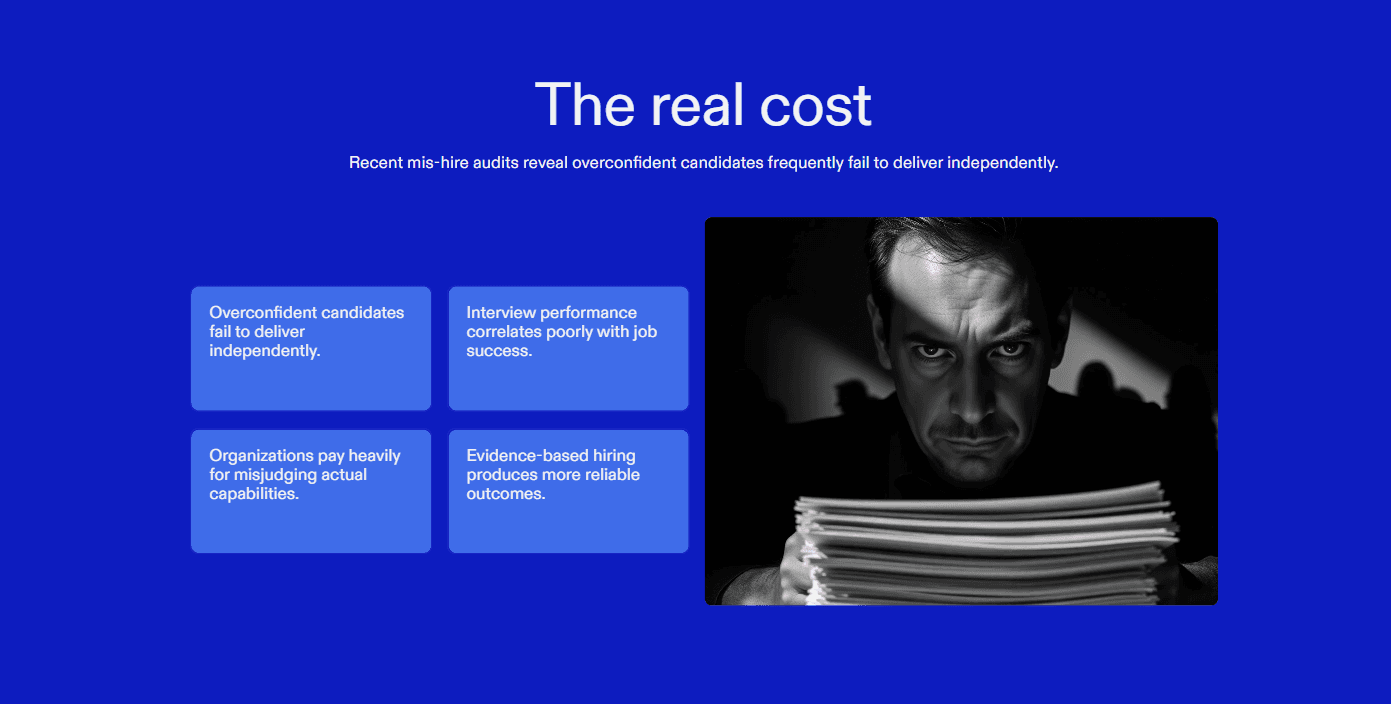
Applying Zero Trust Controls to Hiring
1. Identity and Authorship Verification
Confirm the person demonstrating the skill is the same person who will perform the work.
Control Implementation:
Identity continuity checks across rounds
Reasoning signature comparison (Sherlock AI)
No reliance on visual confirmation alone
2. Continuous Reasoning Validation
Skills must be demonstrated, not declared.
Control Implementation:
Ask re-explanations in new framing
Request tradeoff reasoning instead of “what is” statements
Observe adaptability, not vocabulary
3. Role-Based Interview Data Access
Limit exposure to sensitive data and reduce bias.
Control Implementation:
SCIM role provisioning
Scorecards instead of narrative feedback
Interviewers cannot see previous interviewer notes before their evaluation
4. Audit Trail of Evaluation
Decisions must be explainable later.
Control Implementation:
Logging of score submissions
Logging of notes and edits
Logging of data exports and access events
5. Assume Assisted Reasoning
AI assistance is expected. The goal is to measure independence.
Control Implementation:
Scenario shift prompts
“Teach it to a junior” re-framing tests
Reverse reasoning walkthroughs
Where Sherlock AI Fits in Zero Trust Alignment
Sherlock AI acts as the identity and authorship verification layer inside the interview workflow.
Sherlock AI Capability | Zero Trust Function |
|---|---|
Identity continuity analysis | Verify identity continuously |
Reasoning re-explanation patterning | Continuous verification of context integrity |
Structured scorecards and notes | Access governance and evaluation evidence |
Audit log exports | Telemetry and compliance traceability |
Sherlock AI is not anti-AI. It ensures that the thinking behind the answer is genuinely the candidate’s.
Closing Insight
Modern hiring cannot operate on legacy trust assumptions. To protect organizational performance and fairness:
Interviews must verify identity and reasoning, not just record performance.
Interview Integrity is the Zero Trust model applied to talent evaluation.
This is not surveillance. This is evidence-based hiring.



