Back to all blogs
Learn how to spot proxy interviewers in coding rounds with practical tips and behavioral signals.

Abhishek Kaushik
Jan 8, 2026
Proxy interviewing is when someone else performs the technical interview on behalf of the candidate.
It is one of the fastest-growing forms of interview fraud in remote engineering hiring.
This guide explains why it happens, the behavioral and technical signals to watch for, and how to confirm identity without confrontation.
Why Proxy Interviewing Happens
Remote work and contract-based hiring lowered the barriers to impersonation.
Candidates outsource the evaluation phase to a more skilled engineer.
Once hired, they either:
Attempt to learn on the job
Delegate work to the same proxy
Disappear entirely after onboarding
This is not isolated.
It is a service market, with agencies advertising “we pass your coding rounds for you”.
The pattern has emerged alongside remote technical interviews, where identity verification and real-time skill validation are harder to enforce, making proxy participation and assisted coding interviews more feasible.
The Core Weakness Proxies Exploit
Most coding interviews test execution, not understanding.
Proxies are excellent at:
Implementing patterns
Reciting optimal solutions
Performing well under structured problems
But they cannot fake:
Personal thought process
Tradeoff reasoning
Debugging intuition
So detection must focus on reasoning, not correctness.
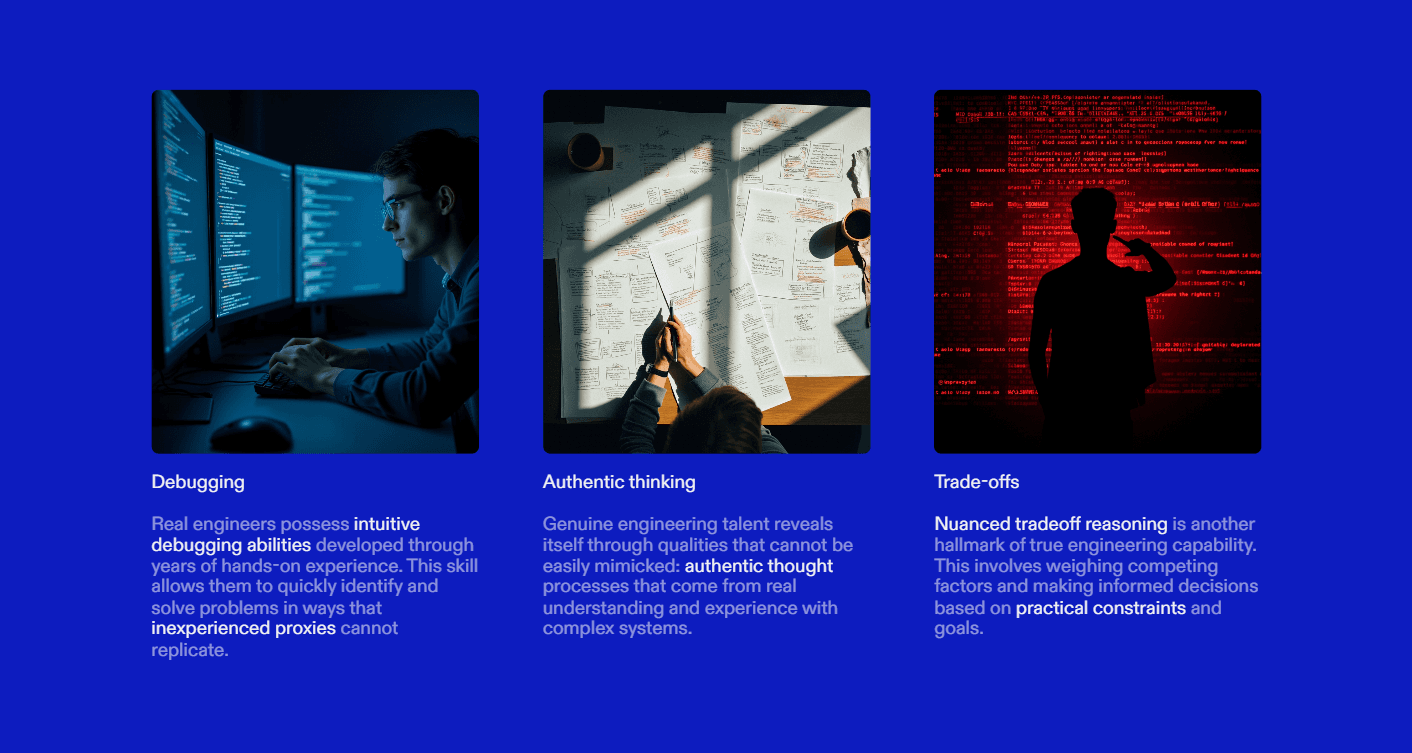
The Detection Framework: Look for Reasoning Stability, Not Output Quality
1. Break the Problem Into Stages
Legitimate candidates
Verbalize reasoning
Show internal structure
Adjust when constraints change
Proxies:
Jump directly to code
Do not share thinking
Resist clarifying questions
Prompt:
Before coding, talk me through how you are thinking about solving this and why.
2. Introduce Constraint Changes Mid-Solution
Example:
Now assume the input size is one million. What changes?
A proxy will:
Struggle to re-evaluate assumptions
Try to return to rehearsed patterns
A real candidate:
Recomputes complexity
Evaluates memory and runtime tradeoffs
Adjusts structure
3. Ask for a Debug Walkthrough
Not “fix this bug”.
Ask:
Where is this most likely to fail and why?
A proxy often:
Cannot evaluate failure states
Relies on pattern memory
A real engineer:
Mentally simulates execution
Mentions edge cases
4. Test for Ownership of Experience
Ask:
Where did you learn this pattern?
What alternative approaches did you consider?
A real candidate recalls:
Team discussions
Mentors
Code reviews
A proxy answers:
General textbook phrasing
Memorized jargon
5. Request Implementation of a Variation
Example:
Now rewrite the solution to support streaming data instead of a static array.
This forces:
Architectural reasoning
Perspective shift
Proxies cannot adapt fluidly.
They revert to the original pattern.
Behavioral and Environmental Signals in Video
Signal | Meaning |
|---|---|
Eye gaze frequently shifting to the side | Reading or receiving prompts |
Slight audio lag followed by fast answers | Relay assistance |
Candidate refuses to turn their head or adjust the camera | Avoiding identity verification |
Keyboard sound mismatch (laptop visible, typing silent) | External person typing |
Candidate types are swift but cannot explain their decisions | Mechanical execution vs understanding |
These are signals to probe, not proof.
Identity Verification Without Confrontation
Use neutral language:
For consistency across candidates, we do a quick identity verification step. Could you briefly show your workspace and confirm your audio source?
If they refuse:
Pause the interview
Require a follow-up verification session
Do not accuse.
Do not challenge.
Just follow the procedure.
Documentation Template (Legal Safe)
Write what happened, not what you think happened.
Conclusion
Proxy interviewing is detectable.
Not through surveillance.
But through reasoning depth, adaptability, debugging intuition, and narrative ownership.
Do not test what they can write.
Test how they think.



